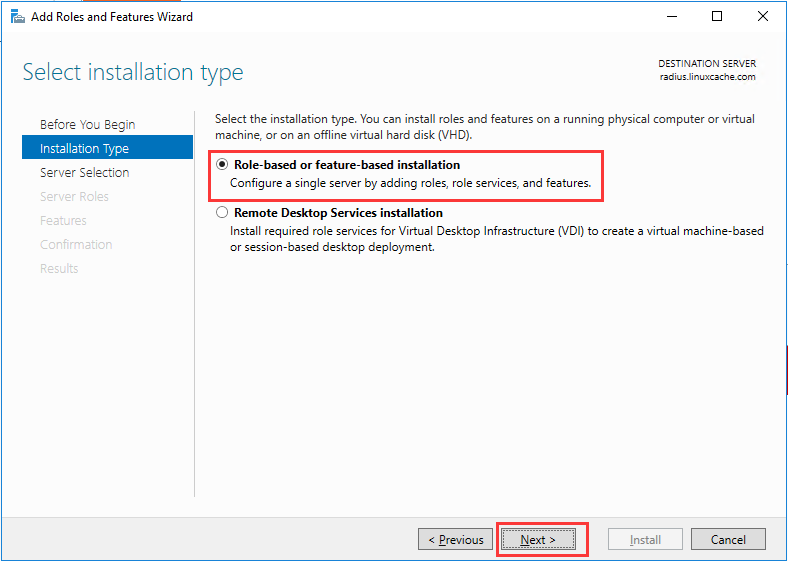
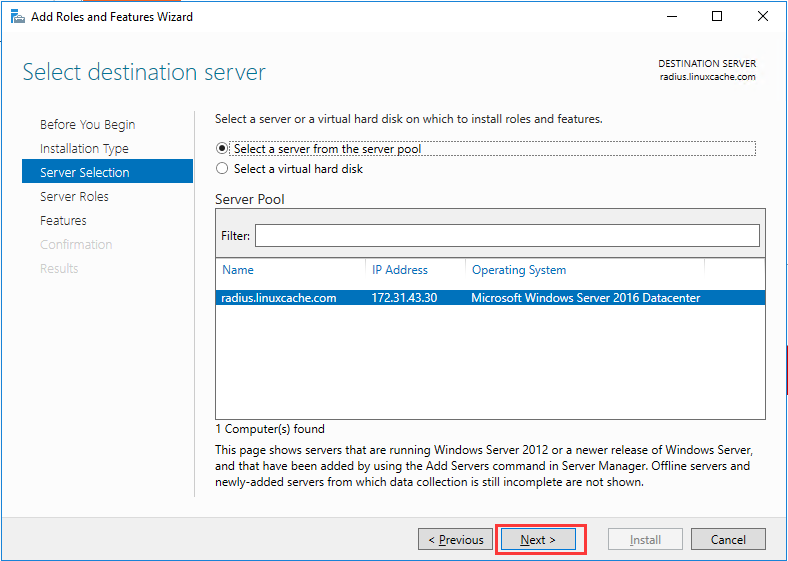
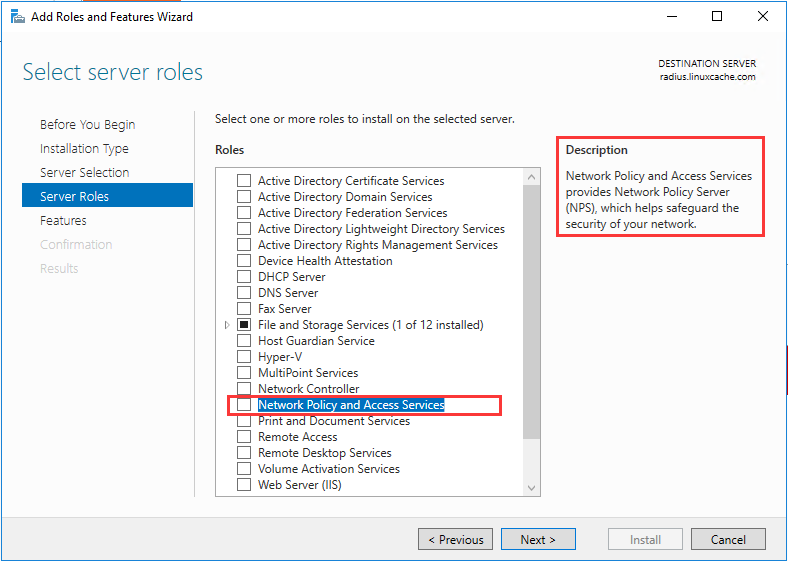
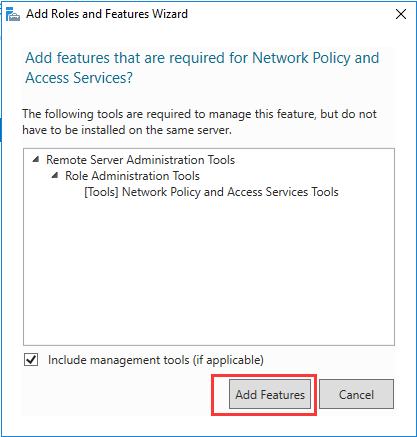
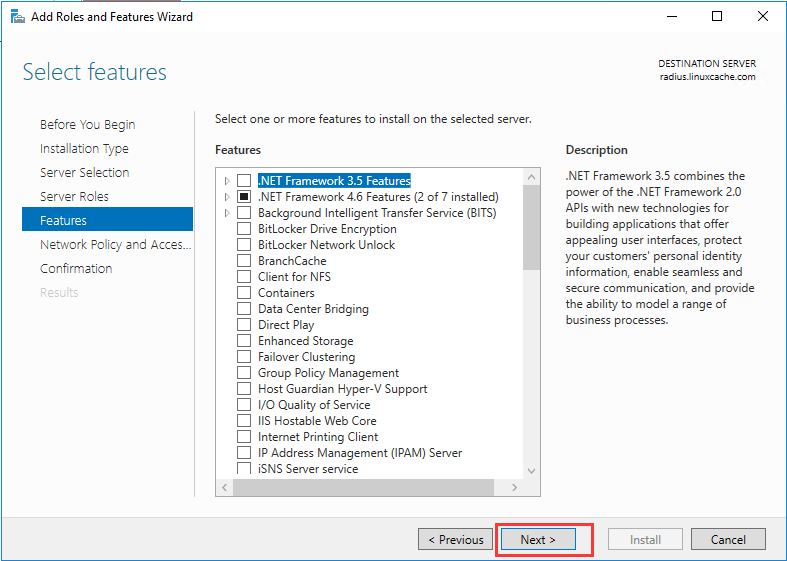
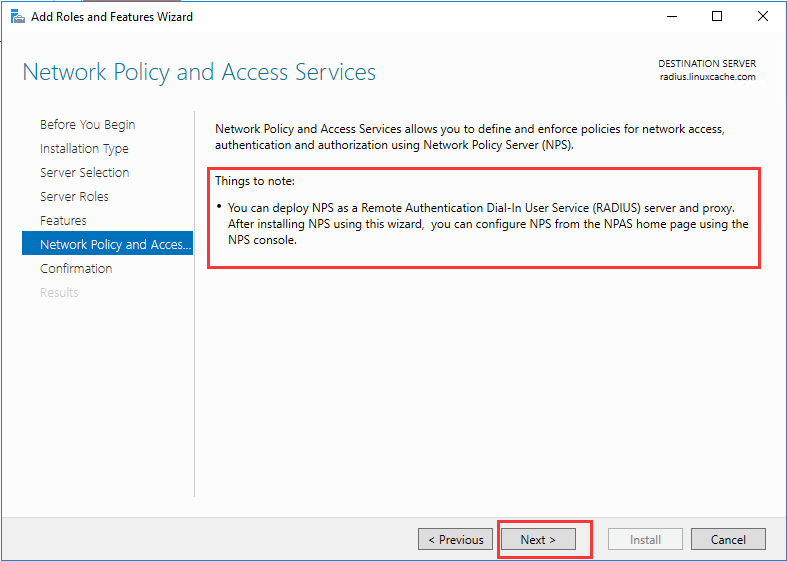
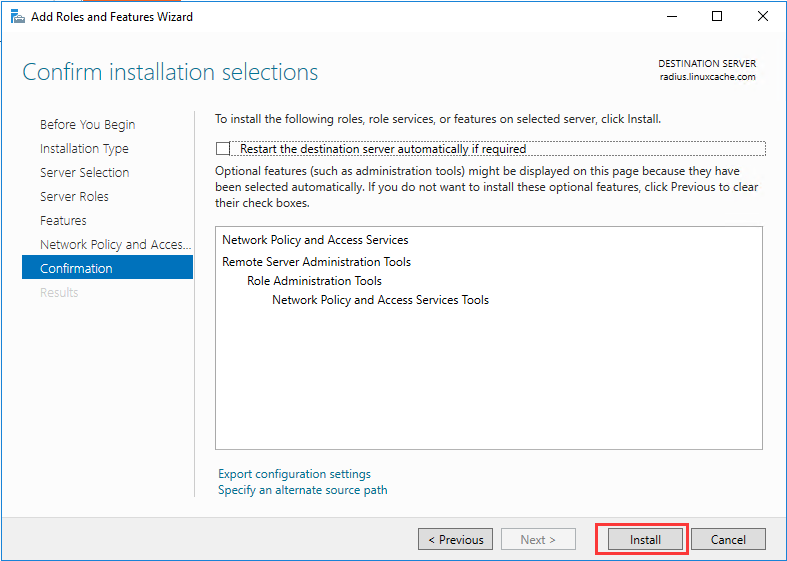
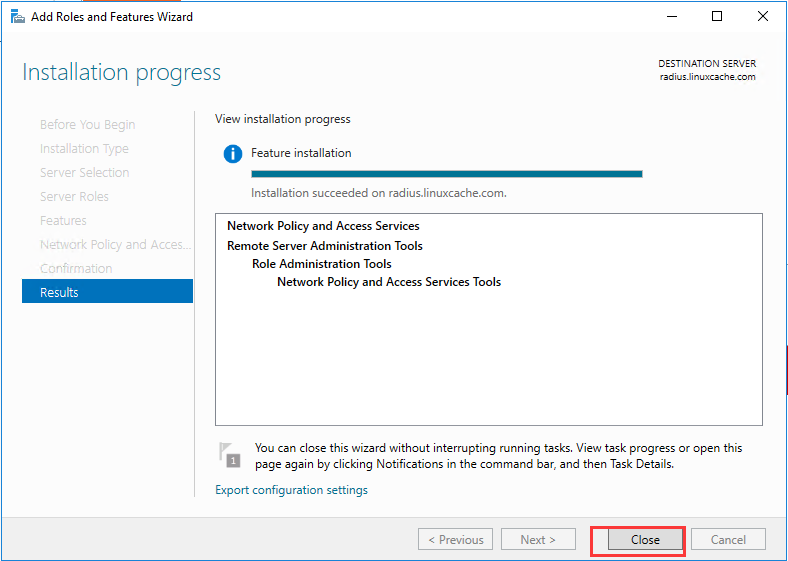
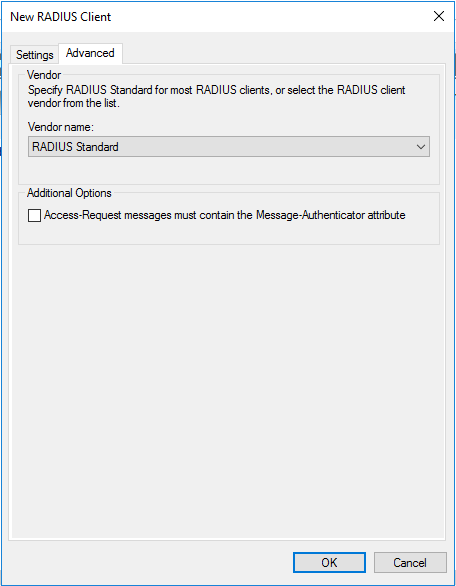
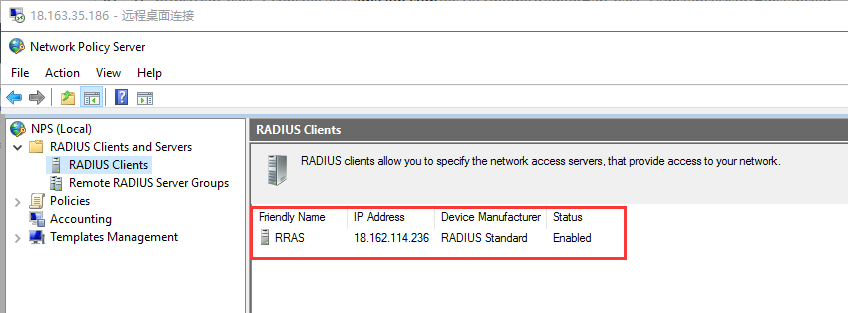
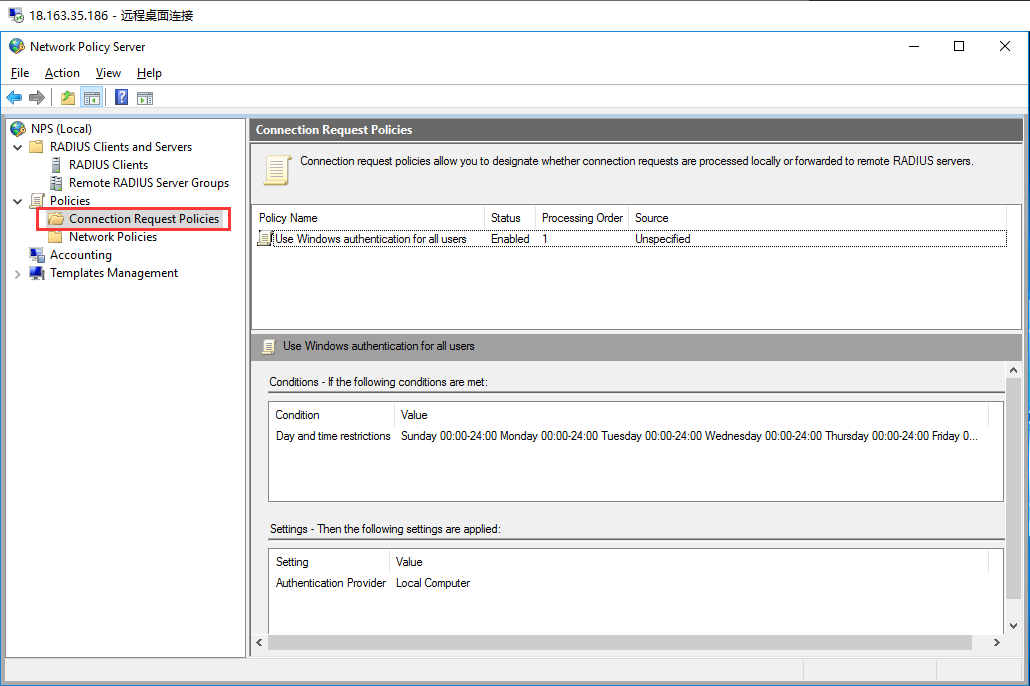
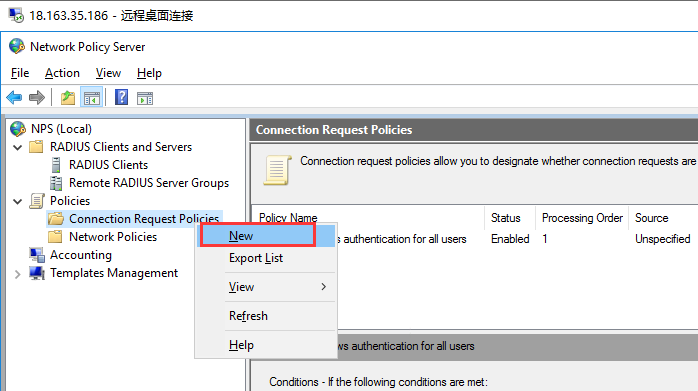
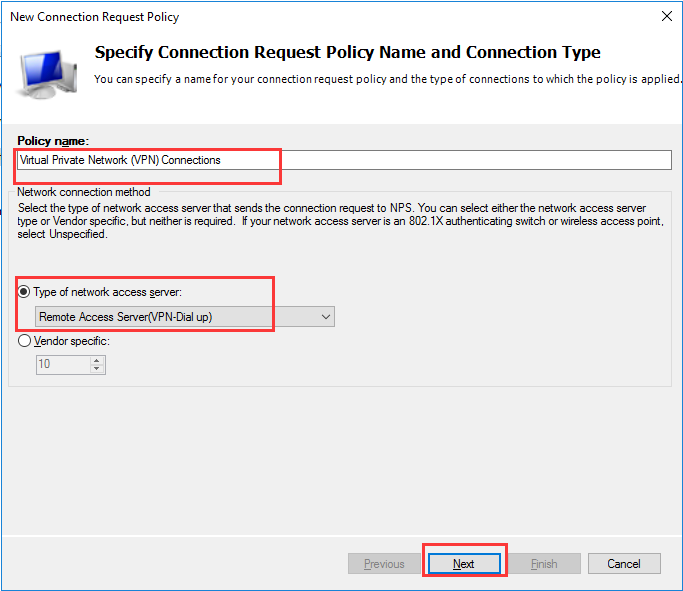
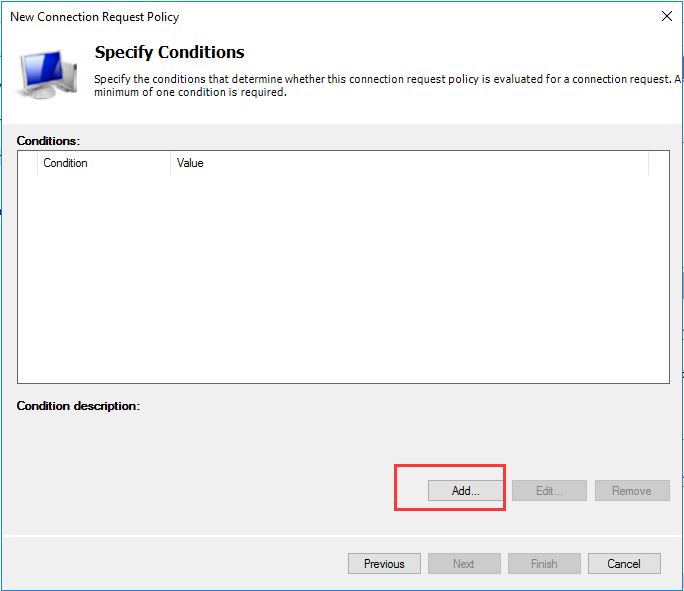
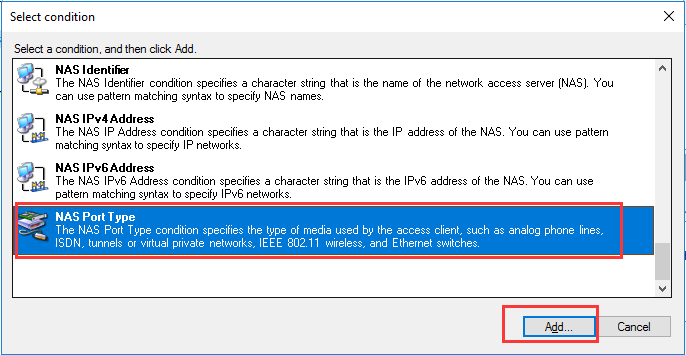
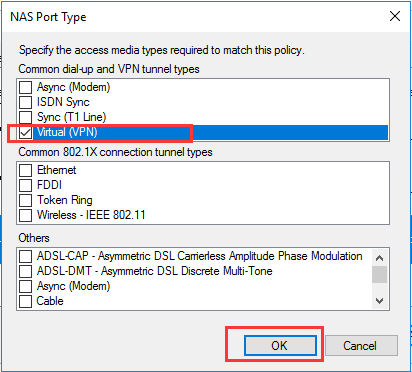
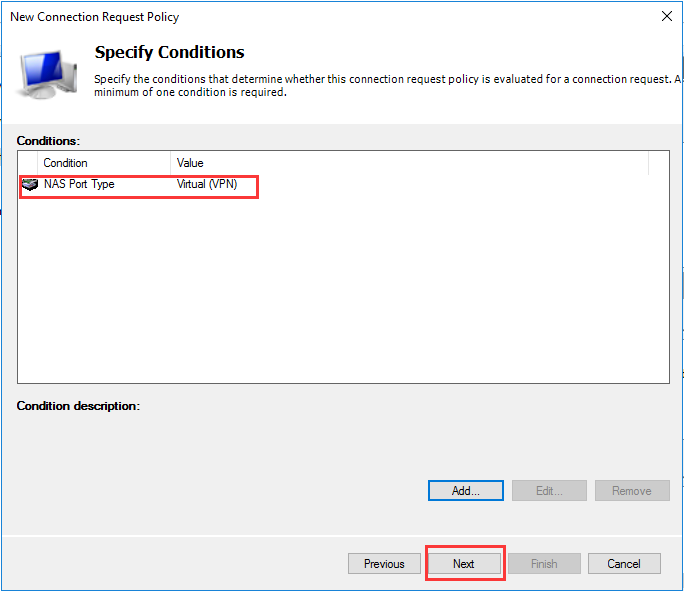
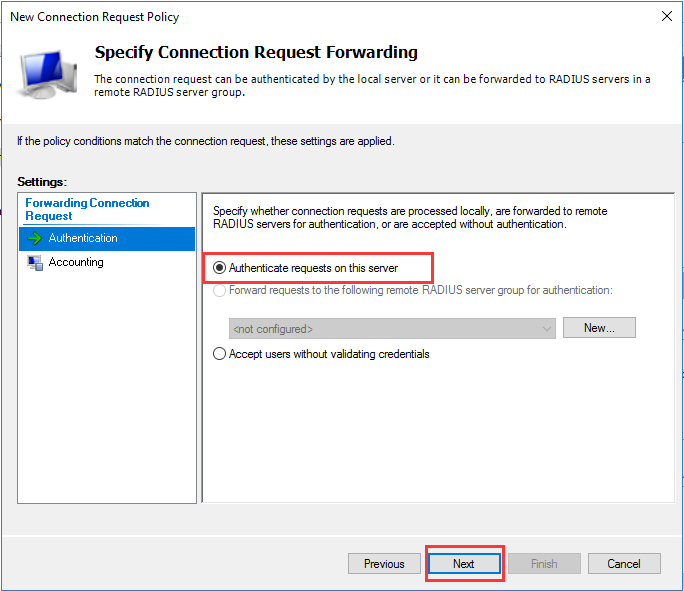
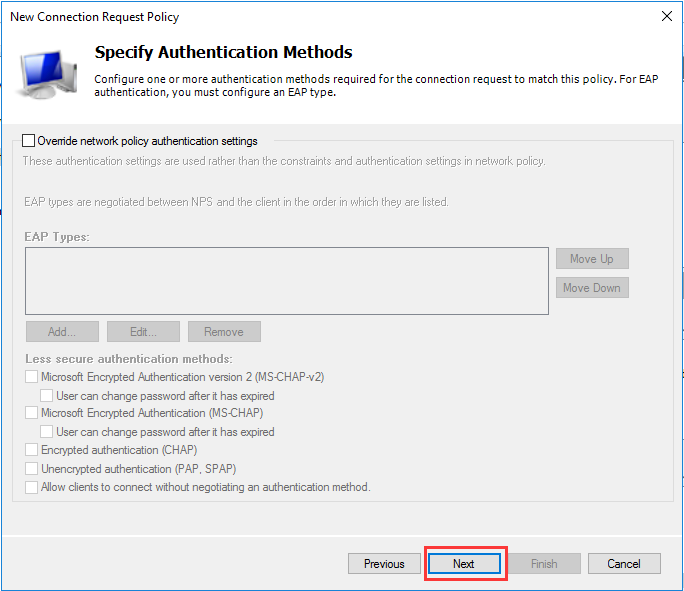
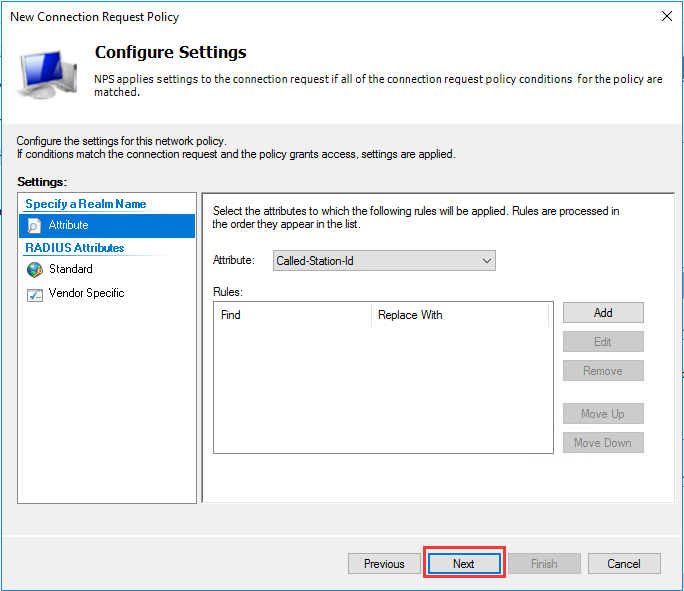
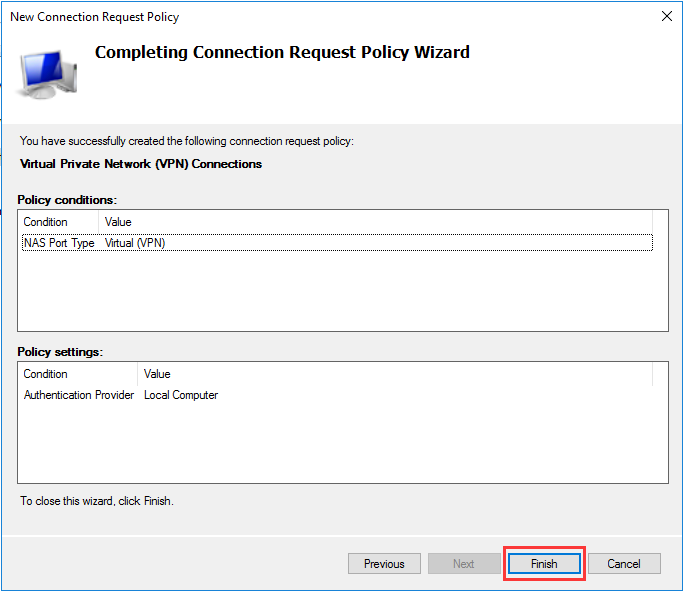
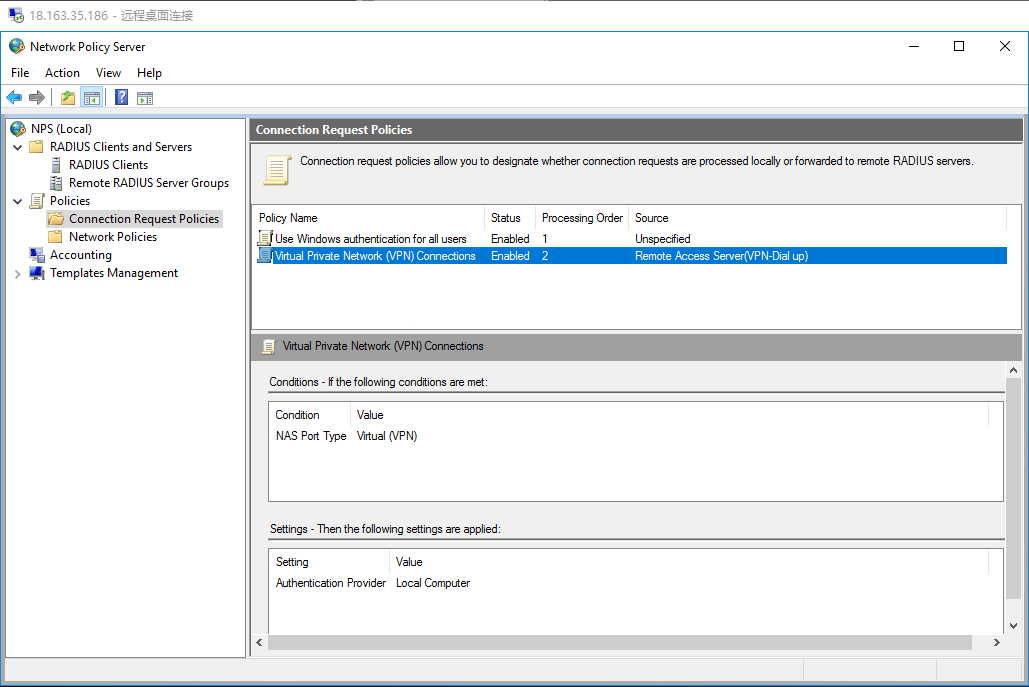
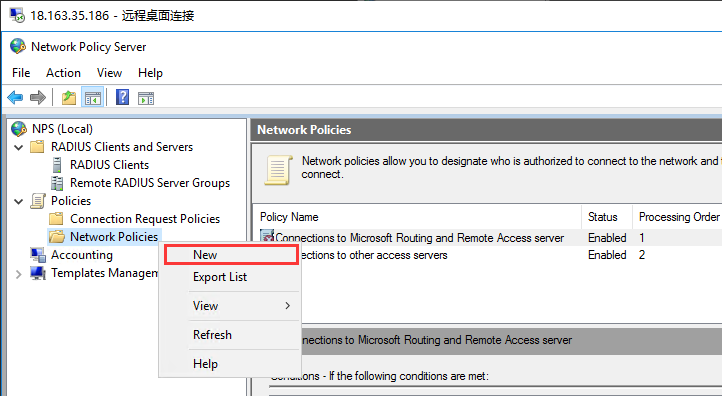
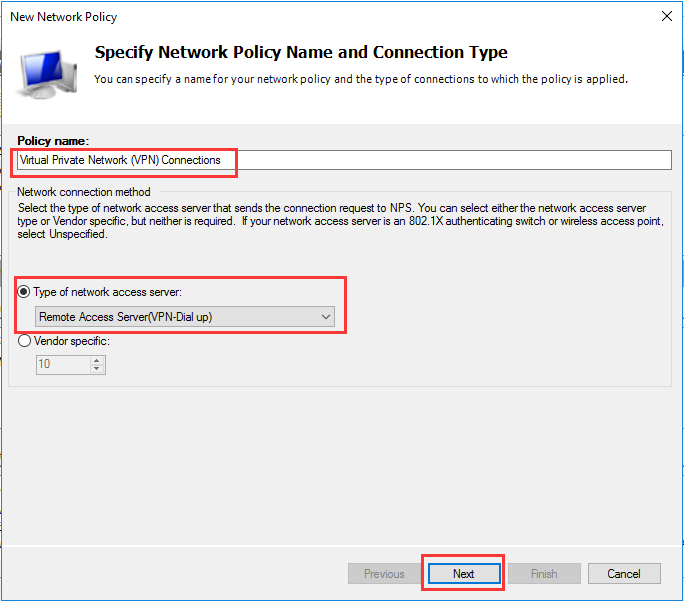
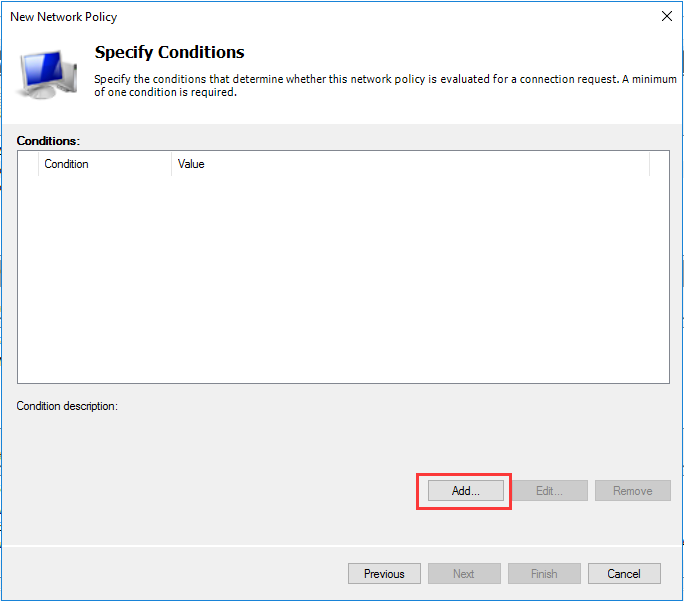
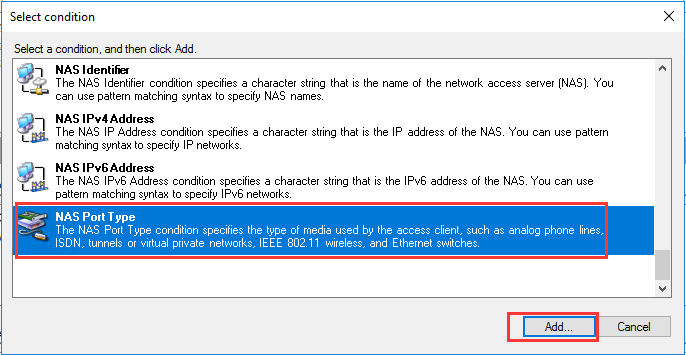
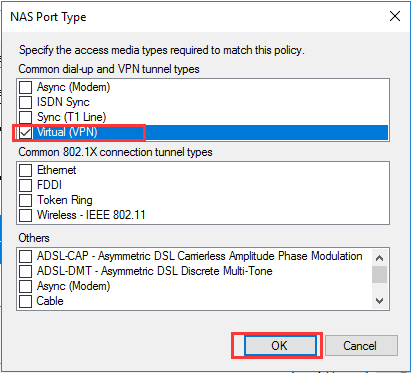
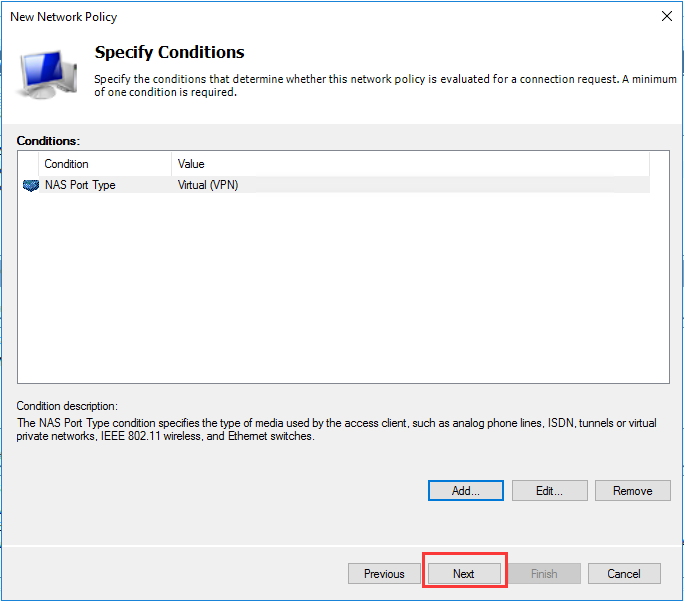
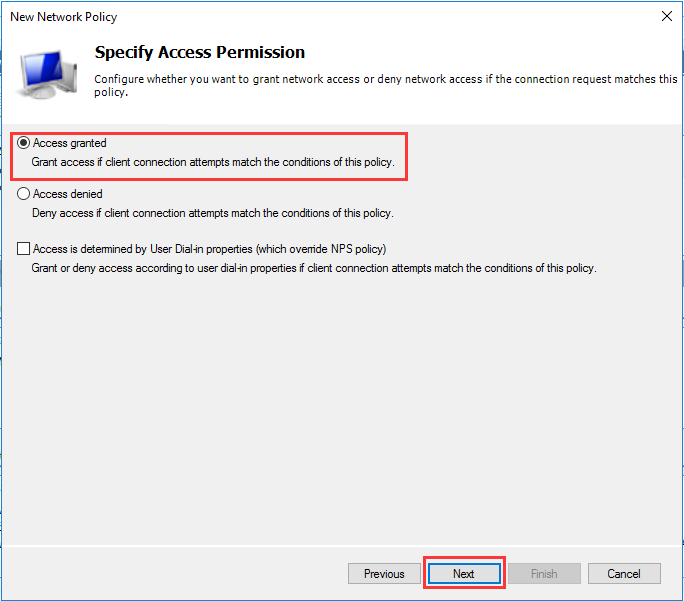
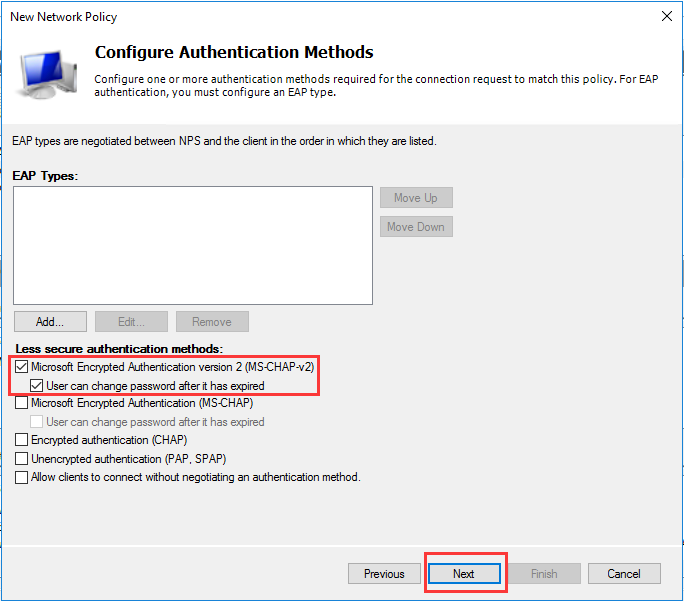
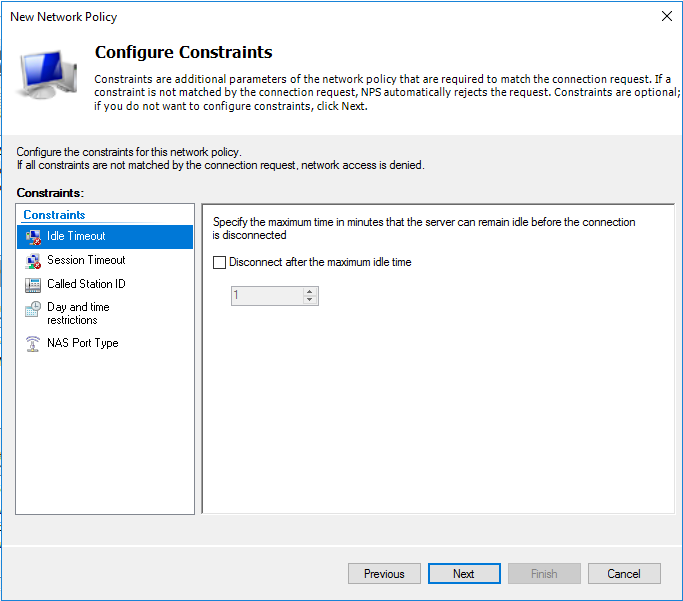
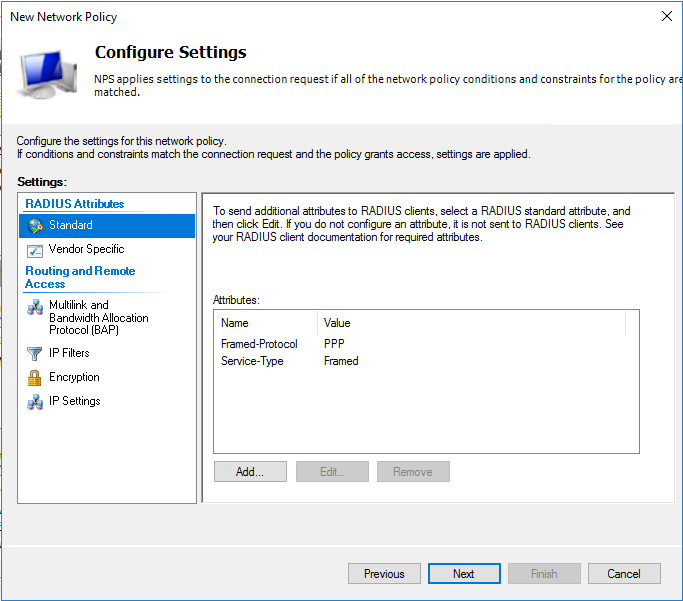
生成客户端私钥
openssl genrsa -aes256 \ -out intermediate/private/device.key.pem 2048 [root@ip-172-31-2-174 ca]# openssl genrsa -aes256 \ > -out intermediate/private/device.key.pem 2048 Generating RSA private key, 2048 bit long modulus ...............+++ ...................................................................+++ e is 65537 (0x10001) Enter pass phrase for intermediate/private/device.key.pem: Verifying - Enter pass phrase for intermediate/private/device.key.pem: [root@ip-172-31-2-174 ca]# chmod 400 intermediate/private/device.key.pem [root@ip-172-31-2-174 ca]#
生成客户端CSR记录
openssl req -config intermediate/openssl.cnf \ -key intermediate/private/device.key.pem \ -new -sha256 -out intermediate/csr/device.csr.pem [root@ip-172-31-2-174 ca]# openssl req -config intermediate/openssl.cnf \ > -key intermediate/private/device.key.pem \ > -new -sha256 -out intermediate/csr/device.csr.pem Enter pass phrase for intermediate/private/device.key.pem: You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [GB]:CN State or Province Name [England]:Guangdong Locality Name []:Shenzhen Organization Name [Alice Ltd]:MENGNIU Organizational Unit Name []:IT Common Name []:IOTHS0000238 Email Address []: [root@ip-172-31-2-174 ca]#
生成客户端证书
openssl ca -config intermediate/openssl.cnf \ -extensions usr_cert -days 180 -notext -md sha256 \ -in intermediate/csr/device.csr.pem \ -out intermediate/certs/device.cert.pem [root@ip-172-31-2-174 ca]# openssl ca -config intermediate/openssl.cnf \ > -extensions usr_cert -days 180 -notext -md sha256 \ > -in intermediate/csr/device.csr.pem \ > -out intermediate/certs/device.cert.pem Using configuration from intermediate/openssl.cnf Enter pass phrase for /root/ca/intermediate/private/intermediate.key.pem: Check that the request matches the signature Signature ok Certificate Details: Serial Number: 4097 (0x1001) Validity Not Before: Mar 21 06:04:03 2020 GMT Not After : Sep 17 06:04:03 2020 GMT Subject: countryName = CN stateOrProvinceName = Guangdong localityName = Shenzhen organizationName = MENGNIU organizationalUnitName = IT commonName = IOTHS0000238 X509v3 extensions: X509v3 Basic Constraints: CA:FALSE Netscape Cert Type: SSL Client, S/MIME Netscape Comment: OpenSSL Generated Client Certificate X509v3 Subject Key Identifier: 27:65:F1:14:2F:E9:F8:41:9F:45:B6:79:32:E7:6C:D5:5C:DE:D3:71 X509v3 Authority Key Identifier: keyid:80:81:95:8B:B9:21:57:07:AE:5E:E2:0A:2C:EE:88:2D:B6:DB:EF:EF X509v3 Key Usage: critical Digital Signature, Non Repudiation, Key Encipherment X509v3 Extended Key Usage: TLS Web Client Authentication, E-mail Protection Certificate is to be certified until Sep 17 06:04:03 2020 GMT (180 days) Sign the certificate? [y/n]:y 1 out of 1 certificate requests certified, commit? [y/n]y Write out database with 1 new entries Data Base Updated [root@ip-172-31-2-174 ca]#
查看证书签发列表
[root@ip-172-31-2-174 ca]# cat intermediate/index.txt V 210321055837Z 1000 unknown /C=CN/ST=Guangdong/L=Shenzhen/O=YSWL/OU=IT/CN=api.iot.com V 200917060403Z 1001 unknown /C=CN/ST=Guangdong/L=Shenzhen/O=MENGNIU/OU=IT/CN=IOTHS0000238 [root@ip-172-31-2-174 ca]#
验证客户端证书信息(180天)
[root@ip-172-31-2-174 ca]# openssl x509 -in intermediate/certs/device.cert.pem -text -noout Certificate: Data: Version: 3 (0x2) Serial Number: 4097 (0x1001) Signature Algorithm: sha256WithRSAEncryption Issuer: C=CN, ST=Guangdong, O=YSWM, OU=YSWM Certificate Authority, CN=YSWM Intermediate CA Validity Not Before: Mar 21 06:04:03 2020 GMT Not After : Sep 17 06:04:03 2020 GMT Subject: C=CN, ST=Guangdong, L=Shenzhen, O=MENGNIU, OU=IT, CN=IOTHS0000238 Subject Public Key Info: Public Key Algorithm: rsaEncryption Public-Key: (2048 bit) Modulus: 00:c7:23:0a:d9:b9:37:8b:6f:41:50:2b:2b:a0:c4: 21:2a:a8:70:65:a3:ea:39:46:4b:76:09:2c:31:5b: a5:a1:b1:08:fc:db:f4:28:5b:b6:fe:08:b6:04:bf: 31:4c:57:0a:06:31:bb:b6:01:1d:94:91:4c:bf:da: 5e:9a:fb:1e:30:d8:52:0e:96:71:9e:68:e2:2e:f7: 20:02:2d:09:7e:54:14:1d:a0:0b:e4:7d:85:ef:51: 14:4d:1d:a6:c4:1c:9c:0e:aa:82:ba:a9:b4:aa:9d: de:f5:c2:3f:80:d6:e3:24:99:18:a2:59:11:a3:64: f9:7f:63:f9:18:42:6d:22:46:f1:a2:8b:86:8a:28: 05:5e:32:3e:da:5f:62:25:38:ea:02:5e:9e:7e:8e: c9:5d:f1:ec:4e:cc:e1:32:5f:ad:59:e2:df:d5:58: a5:29:8a:01:b1:c4:b5:ee:43:78:bb:4b:78:34:41: 5a:cb:56:8d:b2:56:a8:f8:f2:05:be:5f:63:f5:0b: 98:30:22:20:fb:e9:b5:16:85:b9:fe:99:33:3c:d9: da:3c:26:01:a8:a8:d4:9d:31:fd:27:72:87:f6:4a: c0:27:64:e6:89:b8:90:fa:8e:8f:be:e3:f5:80:13: fd:46:bc:0a:e5:43:cc:61:4e:da:15:dd:2f:8d:f6: 15:31 Exponent: 65537 (0x10001) X509v3 extensions: X509v3 Basic Constraints: CA:FALSE Netscape Cert Type: SSL Client, S/MIME Netscape Comment: OpenSSL Generated Client Certificate X509v3 Subject Key Identifier: 27:65:F1:14:2F:E9:F8:41:9F:45:B6:79:32:E7:6C:D5:5C:DE:D3:71 X509v3 Authority Key Identifier: keyid:80:81:95:8B:B9:21:57:07:AE:5E:E2:0A:2C:EE:88:2D:B6:DB:EF:EF X509v3 Key Usage: critical Digital Signature, Non Repudiation, Key Encipherment X509v3 Extended Key Usage: TLS Web Client Authentication, E-mail Protection Signature Algorithm: sha256WithRSAEncryption 39:bb:70:3a:c0:00:19:dd:7d:1c:47:76:cf:d6:31:c0:e6:25: 37:9e:ba:d9:45:59:fd:fc:fb:22:6d:d1:f8:5b:1b:47:0c:79: 06:5a:6f:59:0c:e8:66:d1:b2:c6:17:8d:39:22:d5:a2:69:28: 85:a5:8b:b7:bf:57:8b:45:b8:92:2b:4c:07:2c:7e:c9:c6:e7: cf:9e:4f:b7:42:44:04:8b:e1:11:ea:d5:75:5f:7d:c8:e9:70: c8:12:bf:44:e2:0c:e9:53:72:e8:2f:6f:c7:25:7f:a3:38:5b: 7d:12:90:ec:a5:f3:77:2c:b1:75:f8:3c:87:96:60:3e:ba:84: 7e:aa:79:e6:dc:45:89:70:15:6c:44:d7:e1:24:e0:f7:d5:33: 05:2c:3b:8a:b5:07:b0:6a:41:3f:57:d7:ef:74:05:5d:b7:7a: dc:0a:e1:ae:d4:22:cc:5d:5a:85:da:f9:51:db:a6:56:46:e2: a4:dc:e3:5d:ac:a4:ce:39:8c:cf:db:c1:d1:83:0e:97:30:2e: 29:79:d9:49:75:b5:eb:64:72:8f:cb:35:80:61:46:5e:3a:f4: 4a:50:4f:bf:92:64:a0:91:63:d4:58:db:20:16:f8:67:75:e5: 71:f4:de:fd:99:d8:a7:e5:5b:a3:11:be:d1:76:78:22:89:bf: 49:55:cf:b1:8f:ca:67:91:e4:71:64:8c:fc:1c:bc:eb:15:2b: 92:4b:01:13:30:1d:43:8f:ae:4b:e5:7f:ab:60:be:36:fb:c8: 19:93:dc:8a:de:5e:dd:73:32:00:20:45:b3:16:b8:79:95:07: aa:6c:59:4d:d3:8a:48:ac:cd:fb:91:c0:1b:59:93:3d:68:51: 97:ab:b1:09:53:7d:02:08:3a:42:05:62:a4:a8:b3:a0:fc:cc: 98:96:73:0b:82:08:2b:6c:4b:c7:53:70:86:7f:27:ed:ed:57: 59:15:4a:aa:f3:0e:51:c8:03:ec:dc:8d:04:00:a5:4b:77:f8: 7b:ba:0b:1c:71:4f:3a:d7:a9:b2:1b:01:d8:8a:9f:c3:25:89: 58:6c:24:28:8c:37:bb:81:2f:09:eb:67:d6:1f:1f:35:cf:9b: f6:06:20:00:d6:d0:cc:38:91:d8:cc:89:fe:06:94:81:49:22: 4b:85:3a:cd:0f:9a:be:7e:52:fa:94:33:18:84:d9:d2:aa:88: 20:3d:70:54:33:a7:e3:ea:24:c5:c2:79:01:fa:ef:f5:b1:bd: 34:02:f2:79:b5:ba:d7:0f:d3:0c:6b:b0:66:c2:de:c4:f3:50: 06:4c:05:ca:0d:b5:7b:4c:5f:1e:ff:4f:31:7b:2e:a1:43:67: b2:9a:b2:0a:19:35:75:df [root@ip-172-31-2-174 ca]#
使用CA证书链验证客户端证书有效性
[root@ip-172-31-2-174 ca]# openssl verify -CAfile intermediate/certs/ca-chain.cert.pem intermediate/certs/device.cert.pem intermediate/certs/device.cert.pem: OK [root@ip-172-31-2-174 ca]#