为jenkins服务配置域名指向
C:\Users\harveymei>ping jenkins.bcoc.site
正在 Ping jenkins.bcoc.site [18.162.148.195] 具有 32 字节的数据:
来自 18.162.148.195 的回复: 字节=32 时间=169ms TTL=46
来自 18.162.148.195 的回复: 字节=32 时间=153ms TTL=46
来自 18.162.148.195 的回复: 字节=32 时间=168ms TTL=46
来自 18.162.148.195 的回复: 字节=32 时间=167ms TTL=46
18.162.148.195 的 Ping 统计信息:
数据包: 已发送 = 4,已接收 = 4,丢失 = 0 (0% 丢失),
往返行程的估计时间(以毫秒为单位):
最短 = 153ms,最长 = 169ms,平均 = 164ms
C:\Users\harveymei>
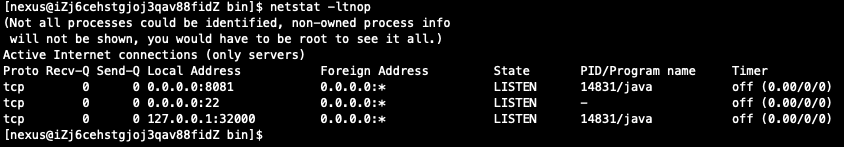
安装完成后启动jenkins服务并查看端口监听
[root@ip-172-31-40-41 ~]# service jenkins start
Starting jenkins (via systemctl): [ OK ]
[root@ip-172-31-40-41 ~]# netstat -lnt
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State
tcp 0 0 0.0.0.0:111 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:25 0.0.0.0:* LISTEN
tcp6 0 0 :::111 :::* LISTEN
tcp6 0 0 :::8080 :::* LISTEN
tcp6 0 0 :::22 :::* LISTEN
tcp6 0 0 ::1:25 :::* LISTEN
[root@ip-172-31-40-41 ~]#
使用浏览器访问未启用SSL加密的Web控制台

申请Let’s Encrypt证书
[root@ip-172-31-40-41 ~]# yum -y install certbot
[root@ip-172-31-40-41 ~]# certbot certonly
Saving debug log to /var/log/letsencrypt/letsencrypt.log
How would you like to authenticate with the ACME CA?
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
1: Spin up a temporary webserver (standalone)
2: Place files in webroot directory (webroot)
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Select the appropriate number [1-2] then [enter] (press 'c' to cancel): 1
Plugins selected: Authenticator standalone, Installer None
Enter email address (used for urgent renewal and security notices) (Enter 'c' to
cancel): harvey.mei@linuxcache.com
Starting new HTTPS connection (1): acme-v02.api.letsencrypt.org
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Please read the Terms of Service at
https://letsencrypt.org/documents/LE-SA-v1.2-November-15-2017.pdf. You must
agree in order to register with the ACME server at
https://acme-v02.api.letsencrypt.org/directory
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
(A)gree/(C)ancel: A
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Would you be willing to share your email address with the Electronic Frontier
Foundation, a founding partner of the Let's Encrypt project and the non-profit
organization that develops Certbot? We'd like to send you email about our work
encrypting the web, EFF news, campaigns, and ways to support digital freedom.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
(Y)es/(N)o: Y
Starting new HTTPS connection (1): supporters.eff.org
Please enter in your domain name(s) (comma and/or space separated) (Enter 'c'
to cancel): jenkins.bcoc.site
Obtaining a new certificate
Performing the following challenges:
http-01 challenge for jenkins.bcoc.site
Waiting for verification...
Cleaning up challenges
IMPORTANT NOTES:
- Congratulations! Your certificate and chain have been saved at:
/etc/letsencrypt/live/jenkins.bcoc.site/fullchain.pem
Your key file has been saved at:
/etc/letsencrypt/live/jenkins.bcoc.site/privkey.pem
Your cert will expire on 2020-05-24. To obtain a new or tweaked
version of this certificate in the future, simply run certbot
again. To non-interactively renew *all* of your certificates, run
"certbot renew"
- Your account credentials have been saved in your Certbot
configuration directory at /etc/letsencrypt. You should make a
secure backup of this folder now. This configuration directory will
also contain certificates and private keys obtained by Certbot so
making regular backups of this folder is ideal.
- If you like Certbot, please consider supporting our work by:
Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate
Donating to EFF: https://eff.org/donate-le
[root@ip-172-31-40-41 ~]#
转换证书格式(使用certtool命令)
[root@ip-172-31-40-41 ~]# yum -y install gnutls-utils
[root@ip-172-31-40-41 ~]# rpm -lq gnutls-utils
/usr/bin/certtool
/usr/bin/crywrap
/usr/bin/danetool
/usr/bin/gnutls-cli
/usr/bin/gnutls-cli-debug
/usr/bin/gnutls-serv
/usr/bin/ocsptool
/usr/bin/p11tool
/usr/bin/psktool
/usr/bin/tpmtool
/usr/share/doc/gnutls-utils-3.3.29
/usr/share/doc/gnutls-utils-3.3.29/certtool.cfg
/usr/share/man/man1/certtool.1.gz
/usr/share/man/man1/danetool.1.gz
/usr/share/man/man1/gnutls-cli-debug.1.gz
/usr/share/man/man1/gnutls-cli.1.gz
/usr/share/man/man1/gnutls-serv.1.gz
/usr/share/man/man1/ocsptool.1.gz
/usr/share/man/man1/p11tool.1.gz
/usr/share/man/man1/psktool.1.gz
/usr/share/man/man1/tpmtool.1.gz
[root@ip-172-31-40-41 ~]#
合并证书公钥私钥为PKCS12格式并设置密码保护(123456)
certtool --to-p12 --load-privkey /etc/letsencrypt/live/jenkins.bcoc.site/privkey.pem \
--pkcs-cipher 3des-pkcs12 \
--load-certificate /etc/letsencrypt/live/jenkins.bcoc.site/fullchain.pem \
--outfile jenkins.p12 --outder
[root@ip-172-31-40-41 ~]# certtool --to-p12 --load-privkey /etc/letsencrypt/live/jenkins.bcoc.site/privkey.pem \
> --pkcs-cipher 3des-pkcs12 \
> --load-certificate /etc/letsencrypt/live/jenkins.bcoc.site/fullchain.pem \
> --outfile jenkins.p12 --outder
Generating a PKCS #12 structure...
Loading private key list...
Loaded 1 private keys.
Enter a name for the key: jenkins.bcoc.site
Enter password:
Confirm password:
[root@ip-172-31-40-41 ~]# ls
anaconda-ks.cfg jenkins.p12 original-ks.cfg
[root@ip-172-31-40-41 ~]#
转换PKCS12格式为JAVA支持的JKS格式
keytool -importkeystore -srckeystore jenkins.p12 \
-srcstorepass '123456' -srcstoretype PKCS12 \
-srcalias jenkins.bcoc.site -deststoretype JKS \
-destkeystore jenkins_keystore.jks \
-deststorepass '123456' -destalias jenkins.bcoc.site
[root@ip-172-31-40-41 ~]# keytool -importkeystore -srckeystore jenkins.p12 \
> -srcstorepass ‘123456’ -srcstoretype PKCS12 \
> -srcalias jenkins.bcoc.site -deststoretype JKS \
> -destkeystore jenkins_keystore.jks \
> -deststorepass ‘123456’ -destalias jenkins.bcoc.site
Importing keystore jenkins.p12 to jenkins_keystore.jks...
keytool error: java.io.IOException: keystore password was incorrect
[root@ip-172-31-40-41 ~]# keytool -importkeystore -srckeystore jenkins.p12 \
> -srcstorepass '123456' -srcstoretype PKCS12 \
> -srcalias jenkins.bcoc.site -deststoretype JKS \
> -destkeystore jenkins_keystore.jks \
> -deststorepass '123456' -destalias jenkins.bcoc.site
Importing keystore jenkins.p12 to jenkins_keystore.jks...
Warning:
The JKS keystore uses a proprietary format. It is recommended to migrate to PKCS12 which is an industry standard format using "keytool -importkeystore -srckeystore jenkins_keystore.jks -destkeystore jenkins_keystore.jks -deststoretype pkcs12".
[root@ip-172-31-40-41 ~]#
[root@ip-172-31-40-41 ~]# ls
anaconda-ks.cfg jenkins_keystore.jks jenkins.p12 original-ks.cfg
[root@ip-172-31-40-41 ~]#
修改证书文件属性
[root@ip-172-31-40-41 ~]# chown jenkins.jenkins jenkins_keystore.jks
[root@ip-172-31-40-41 ~]# chmod 600 jenkins_keystore.jks
[root@ip-172-31-40-41 ~]# mv jenkins_keystore.jks /var/lib/jenkins/
[root@ip-172-31-40-41 ~]#
修改jenins配置文件
[root@ip-172-31-40-41 ~]# vi /etc/sysconfig/jenkins
初始配置文件(SSL部分)
## Type: integer(0:65535)
## Default: ""
## ServiceRestart: jenkins
#
# HTTPS port Jenkins is listening on.
# Default is disabled.
#
JENKINS_HTTPS_PORT=""
## Type: string
## Default: ""
## ServiceRestart: jenkins
#
# Path to the keystore in JKS format (as created by the JDK 'keytool').
# Default is disabled.
#
JENKINS_HTTPS_KEYSTORE=""
## Type: string
## Default: ""
## ServiceRestart: jenkins
#
# Password to access the keystore defined in JENKINS_HTTPS_KEYSTORE.
# Default is disabled.
#
JENKINS_HTTPS_KEYSTORE_PASSWORD=""
## Type: string
## Default: ""
## ServiceRestart: jenkins
#
# IP address Jenkins listens on for HTTPS requests.
# Default is disabled.
#
JENKINS_HTTPS_LISTEN_ADDRESS=""
修改
## Type: integer(0:65535)
## Default: ""
## ServiceRestart: jenkins
#
# HTTPS port Jenkins is listening on.
# Default is disabled.
#
JENKINS_HTTPS_PORT="8443"
## Type: string
## Default: ""
## ServiceRestart: jenkins
#
# Path to the keystore in JKS format (as created by the JDK 'keytool').
# Default is disabled.
#
JENKINS_HTTPS_KEYSTORE="/var/lib/jenkins/jenkins_keystore.jks"
## Type: string
## Default: ""
## ServiceRestart: jenkins
#
# Password to access the keystore defined in JENKINS_HTTPS_KEYSTORE.
# Default is disabled.
#
JENKINS_HTTPS_KEYSTORE_PASSWORD="123456"
## Type: string
## Default: ""
## ServiceRestart: jenkins
#
# IP address Jenkins listens on for HTTPS requests.
# Default is disabled.
#
JENKINS_HTTPS_LISTEN_ADDRESS="0.0.0.0"
禁用8080端口监听
初始配置文件
## Type: integer(0:65535)
## Default: 8080
## ServiceRestart: jenkins
#
# Port Jenkins is listening on.
# Set to -1 to disable
#
JENKINS_PORT="8080"
修改(禁用8080端口监听)
## Type: integer(0:65535)
## Default: 8080
## ServiceRestart: jenkins
#
# Port Jenkins is listening on.
# Set to -1 to disable
#
JENKINS_PORT="-1"
重启服务并查看端口监听变化
[root@ip-172-31-40-41 ~]# service jenkins restart
Restarting jenkins (via systemctl): [ OK ]
[root@ip-172-31-40-41 ~]# netstat -lnt
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State
tcp 0 0 0.0.0.0:111 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:25 0.0.0.0:* LISTEN
tcp6 0 0 :::111 :::* LISTEN
tcp6 0 0 :::22 :::* LISTEN
tcp6 0 0 ::1:25 :::* LISTEN
tcp6 0 0 :::8443 :::* LISTEN
[root@ip-172-31-40-41 ~]#
使用https协议及配置端口访问jenkins服务控制台

使用openssl命令合并公钥私钥为PKCS12命令用法
openssl pkcs12 -export -out jenkins.p12 \
-passout 'pass:123456' -inkey /etc/letsencrypt/live/jenkins.bcoc.site/privkey.pem \
-in /etc/letsencrypt/live/jenkins.bcoc.site/fullchain.pem \
-name jenkins.bcoc.site


 选择对应操作系统版本点击下载
选择对应操作系统版本点击下载





 启动nexu服务并查看运行状态
启动nexu服务并查看运行状态