1 月 222020

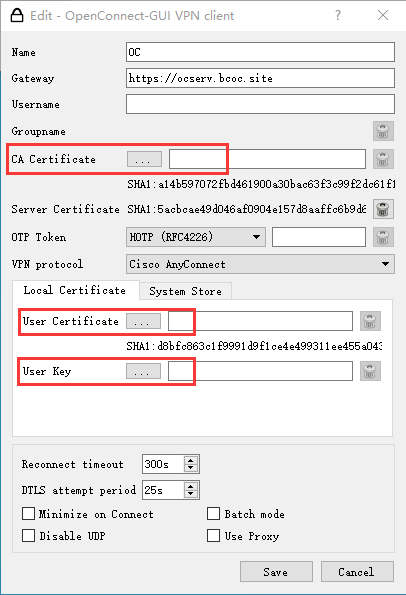
使用自签证书进行用户身份验证,使用Let’s Encrypt权威证书作为服务器证书
启用内核包转发
[root@ocserv ~]# echo "net.ipv4.ip_forward = 1" >> /etc/sysctl.conf [root@ocserv ~]# sysctl -p net.ipv6.conf.all.accept_ra = 2 net.ipv6.conf.eth0.accept_ra = 2 net.ipv4.ip_forward = 1 [root@ocserv ~]#
开启防火墙端口及包转发特性
[root@ocserv ~]# firewall-cmd --permanent --add-port=443/tcp success [root@ocserv ~]# firewall-cmd --permanent --add-port=443/udp success [root@ocserv ~]# firewall-cmd --permanent --add-port=80/tcp success [root@ocserv ~]# firewall-cmd --permanent --add-port=8080/tcp success [root@ocserv ~]# firewall-cmd --permanent --add-masquerade success [root@ocserv ~]# firewall-cmd --reload success [root@ocserv ~]#
安装ocserv服务包及Let’s Encrypt工具包
[root@ocserv ~]# yum -y install ocserv certbot
使用certbot生成的服务器证书和密钥路径
/etc/letsencrypt/live/ocserv.bcoc.site/fullchain.pem /etc/letsencrypt/live/ocserv.bcoc.site/privkey.pem
修改ocserv服务端配置
[root@ocserv ~]# vi /etc/ocserv/ocserv.conf
修改认证类型为证书认证
auth = "certificate"
修改服务器证书配置
server-cert = /etc/letsencrypt/live/ocserv.bcoc.site/fullchain.pem server-key = /etc/letsencrypt/live/ocserv.bcoc.site/privkey.pem
修改用户端证书身份识别
#cert-user-oid = 0.9.2342.19200300.100.1.1 cert-user-oid = 2.5.4.3
启用压缩
compression = true no-compress-limit = 256
设置客户端IPv4地址池
ipv4-network = 192.168.172.0 ipv4-netmask = 255.255.255.0
设置DNS
dns = 8.8.8.8 dns = 8.8.4.4
启动服务
[root@ocserv ~]# systemctl start ocserv
安装Apache服务器,为用户证书提供下载服务
[root@ocserv ~]# yum -y install httpd
修改Apache主配置文件并启动服务
[root@ocserv ~]# vi /etc/httpd/conf/httpd.conf
修改主机名
ServerName ocserv.bcoc.site
修改服务监听端口
#Listen 80 Listen 8080
检查配置并启动服务
[root@ocserv ~]# apachectl -t Syntax OK [root@ocserv ~]# systemctl enable httpd Created symlink from /etc/systemd/system/multi-user.target.wants/httpd.service to /usr/lib/systemd/system/httpd.service. [root@ocserv ~]# systemctl start httpd [root@ocserv ~]#
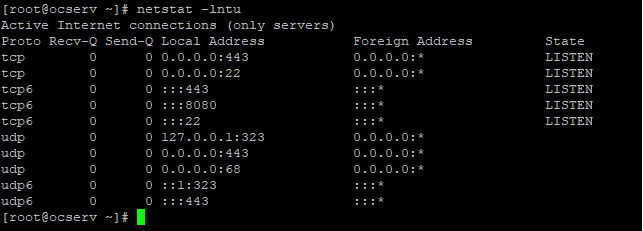
查看监听
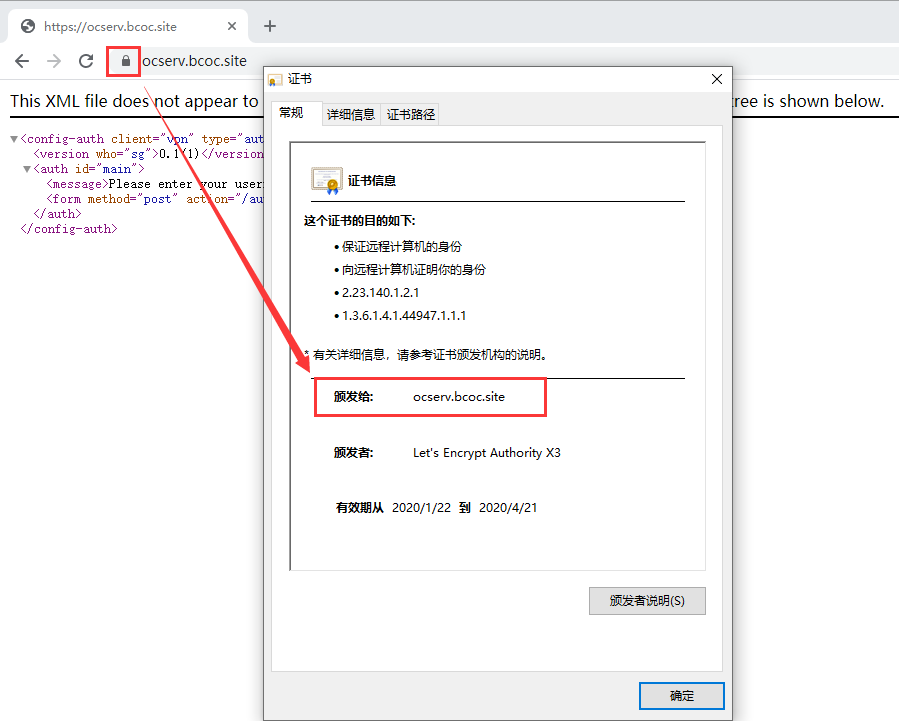
使用浏览器访问服务器端口确认证书状态
生成自签CA证书
[root@ocserv ~]# certtool --generate-privkey --outfile ca-key.pem Generating a 2048 bit RSA private key... [root@ocserv ~]# cat << _EOF_ >ca.tmpl > cn = "BCOC CA" > organization = "BCOC" > serial = 1 > expiration_days = -1 > ca > signing_key > cert_signing_key > crl_signing_key > _EOF_ [root@ocserv ~]# certtool --generate-self-signed --load-privkey ca-key.pem \ > --template ca.tmpl --outfile ca-cert.pem
生成自签用户证书
[root@ocserv ~]# certtool --generate-privkey --outfile user-key.pem Generating a 2048 bit RSA private key... [root@ocserv ~]# cat << _EOF_ >user.tmpl > cn = "harveymei" > unit = "standard" > expiration_days = 365 > signing_key > tls_www_client > _EOF_ [root@ocserv ~]# certtool --generate-certificate --load-privkey user-key.pem \ > --load-ca-certificate ca-cert.pem --load-ca-privkey ca-key.pem \ > --template user.tmpl --outfile user-cert.pem
导出为PKCS12格式,为证书设置密钥(导入证书时需要输入)
[root@ocserv ~]# certtool --to-p12 --load-privkey user-key.pem \ > --pkcs-cipher 3des-pkcs12 \ > --load-certificate user-cert.pem \ > --outfile user.p12 --outder Generating a PKCS #12 structure... Loading private key list... Loaded 1 private keys. Enter a name for the key: harveymei Enter password: Confirm password: [root@ocserv ~]# ls ca-cert.pem ca.tmpl user-key.pem user.tmpl ca-key.pem user-cert.pem user.p12 [root@ocserv ~]#
将用户证书复制到Web Server服务器根目录下以提供证书下载
[root@ocserv ~]# cp user.p12 /var/www/html/
使用自签CA证书覆盖ocserv初始CA证书
[root@ocserv ~]# cp ca-cert.pem /etc/pki/ocserv/cacerts/ca.crt cp: overwrite ‘/etc/pki/ocserv/cacerts/ca.crt’? y
覆盖CA证书后重新启动ocserv服务
[root@ocserv ~]# systemctl restart ocserv
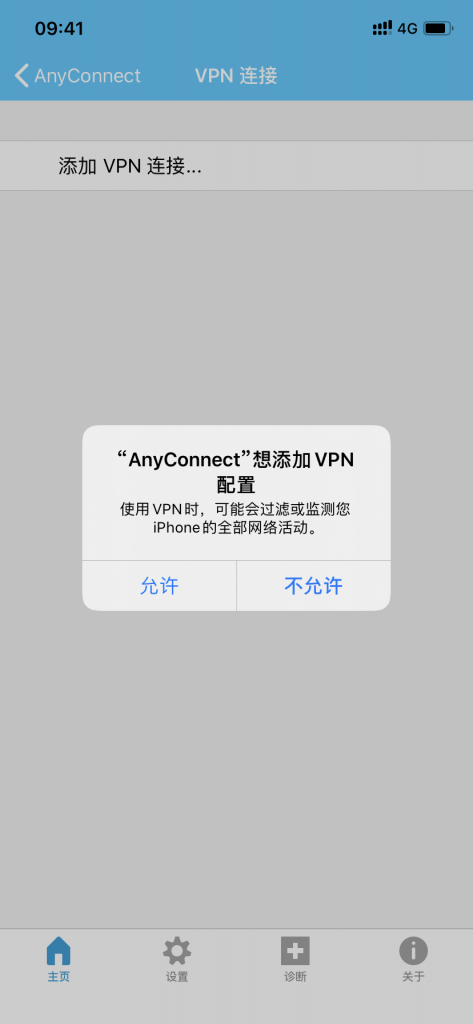
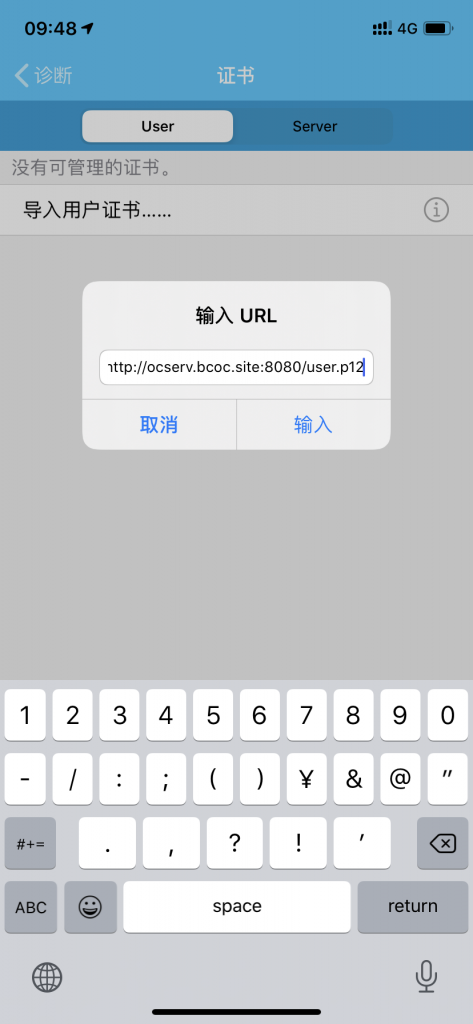
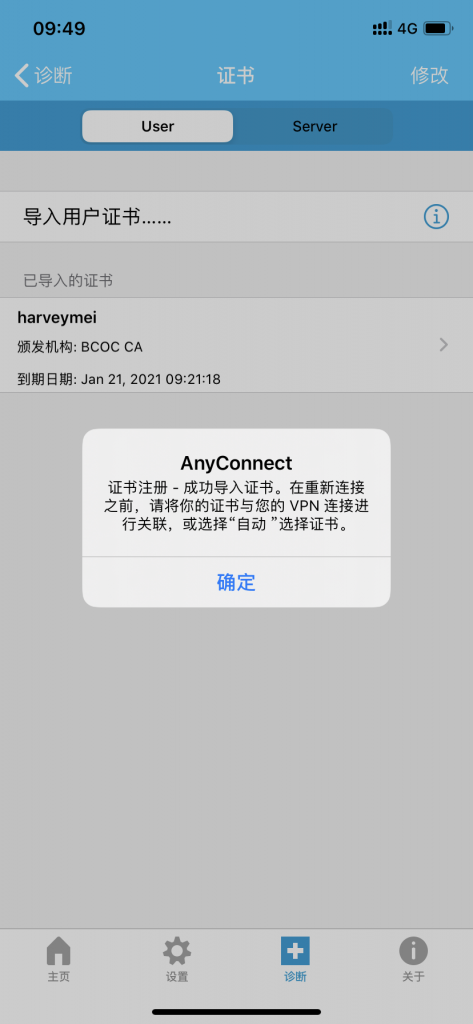
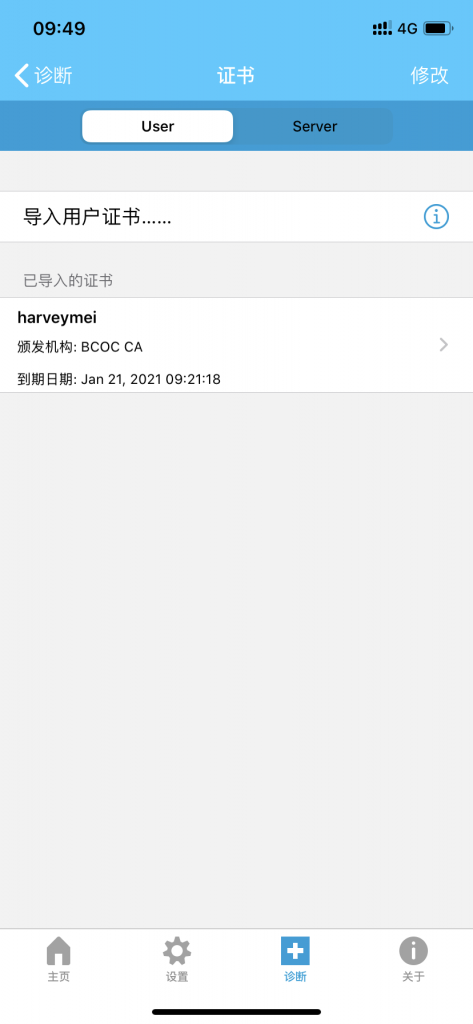
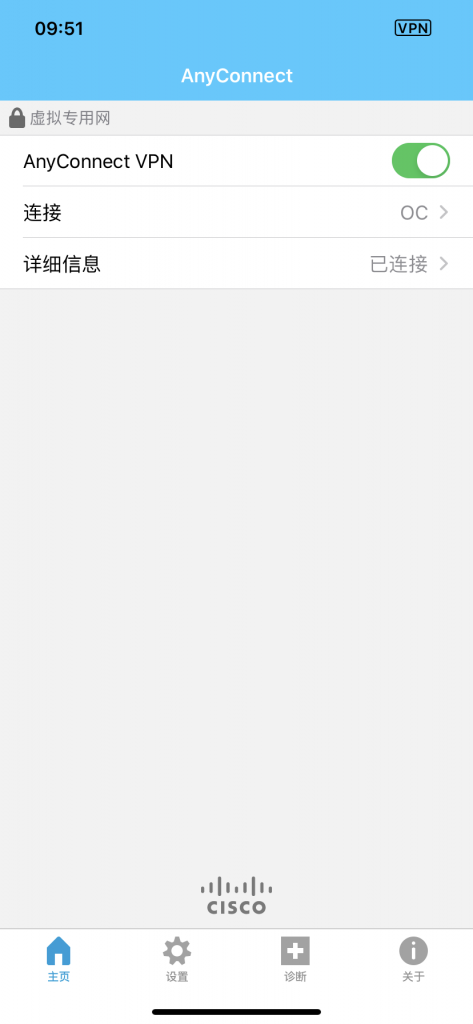
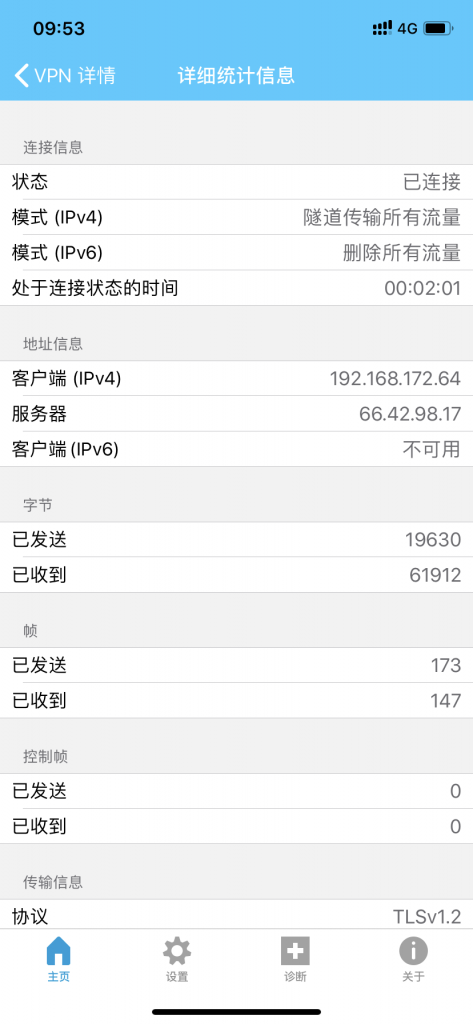
客户端新建连接并导入用户证书
客户端证书下载地址(客户端导入证书需输入密码)
http://ocserv.bcoc.site:8080/user.p12




Windows 10 系统下OpenConnect GUI的设置